
In the rapidly growing landscape of cybersecurity, the part of a Security Operations Center (SOC) Analyst has developed to become increasingly necessary. SOC Analysts are the unacknowledged icons, acting after the settings to rescue associations from the ever-present risk of cyberattacks. But what precisely does a SOC Analyst do? In this guide, we’ll explore the essential parts and responsibilities of a SOC Analyst, alleviating light on the paramount work they perform to keep our digital world secure.
Monitoring and Analyzing Security Events
The essence of a SOC Analyst’s position is the persistent monitoring of protection events. Utilizing various devices and technology, SOC Analysts watch network traffic for alerts of suspicious activity. This aggressive monitoring is required before probable threats are detected.

Tools and Technologies
SOC Analysts use Security Information and Event Management (SIEM) strategies to manage and analyze data from significant references. They also depend on Intrusion Detection Systems (IDS), firewalls, and anti-virus software to catch irregularities and dangerous movements. These tools supply the real-time visibility required to notice and manage threats punctually.
Incident Response and Management
When a security incident occurs, SOC Analysts start to act. They observe predefined protocols to handle and mitigate the incident, ensuring that the threat is prevented and the impacts are minimized. The incident affects an arrangement of steps, including identification, containment, eradication, recovery, and post-incident research.

Incident Response Process
Identification: Detect and verify the security incident.
Containment: Isolate the affected systems to prevent the threat from spreading.
Eradication: Remove the danger from the environment.
Recovery: Restore and validate system functionality.
Post-Incident Analysis: Document the incident and analyze it to prevent future occurrences.
Threat Intelligence and Analysis
Understanding the qualities of threats is necessary for useful security. SOC Analysts contend in threat intelligence and research, collecting data on appearing threats and attack vectors. They study ways, assess vulnerabilities, and develop strategies to counteract conceivable attacks.

Sources of Threat Intelligence
- SOC Analysts collect threat intelligence from an assortment of bases, including:
- Open-source intelligence (OSINT)
- Commercial threat intelligence services
- Internal logs and data
- Collaboration with other cybersecurity professionals
Compliance and Reporting
Compliance with controlling requirements is an essential component of a SOC Analyst’s duties. They ensure that the establishment adheres to functional rules and standards, such as GDPR, HIPAA, or PCI-DSS. Also, SOC Analysts organize complex messages on security experiences, supplying useful understandings that help improve the association’s security posture.

Key Compliance Standards
- General Data Protection Regulation
- Health Insurance Portability and Accountability Act
- Settlement Card Industry Data Protection Standard
Cooperation and Communication
Influential communication is crucial for SOC Analysts, both within their gathering and with additional stakeholders. They must be skilled at expressing complicated technical knowledge in a manner that is readable to non-technical associates. Collaboration with additional IT and security groups is essential to securing a persistent cybersecurity strategy.

Team Dynamics
SOC Analysts usually work in changes to provide a 24/7 range. Teamwork and collaboration are essential, with analysts communicating acuities and strategies to address security challenges effectively. Regular briefings and handovers ensure continuity and a suitable response to dangers.
Continued Learning and Adaptation
The cybersecurity terrain is continuously modifying, and SOC Analysts must stay ahead of the curve. It involves constant learning and transformation, keeping up with the latest threats, devices, and techniques. SOC Analysts frequently participate in activity sessions, certificates, and skilled growth activities to improve their skills and knowledge.
Popular Certifications
- CompTIA Security+
- Certified Information Systems Security Professional
- Certified Ethical Hacker
Skills Must for a SOC Analyst
In cybersecurity, the procedure of a Security Operations Center Analyst is paramount. These professionals protect an association’s digital support, always monitoring for dangers and reacting to incidents. But what does it accept to excel in this assignment? In this guide, we will explore the basic skills required for a SOC Analyst, highlighting the blend of technical prowess, analytical knowledge, and delicate skills that create a successful cybersecurity defender.

Technical Skills
Technical skills form the of a SOC Analyst’s expertise. An in-depth knowledge of myriad cybersecurity tools and technologies is paramount to effectively monitoring, catching, and responding to dangers.
Understanding Network Protocols
A SOC Reviewer must participate in web protocols, such as TCP/IP, HTTP, HTTPS, DNS, and FTP. Learning how data streamlets via a network allows analysts to spot irregularities that could suggest a security threat.
Familiarity with SIEM Systems
Security Information and Event Management (SIEM) procedures are a major feature of a SOC Analyst’s toolkit. These procedures organize and analyze record data from a vast database, delivering a real-time understanding of potential security incidents. The qualification to utilize SIEM apparatuses such as Splunk, ArcSight, or QRadar is instructed.
Implementation of Firewalls and IDS/IPS
Firewalls and Intrusion Detection/Prevention Systems are integral segments of web security. SOC Reviewers are required to comprehend how these techniques function, how to configure them, and how to explore their indications.
Experience with Anti-virus and Endpoint Security Solutions
SOC Analysts should be knowledgeable about various anti-virus and endpoint security explanations. It possesses an understanding of how these devices detect and react to malware, as well as how to interpret and act upon alerts affected by these techniques.
Analytical Skills
Beyond technical know-how, SOC Analysts must possess strong analytical skills. The capability to interpret complex data and recognize patterns is essential for threat detection and incident response.
Log Analysis
SOC Analysts spend significant time examining logs from various considerations, such as firewalls, routers, and waitpeople. The capacity to sift through extended data and recognize relevant safety events is critical.
Threat Intelligence Analysis
Comprehending and analyzing threat intellect is a fundamental feature of a SOC Analyst’s position. It concerns analyzing and considering new threats, understanding their possible impact, and designing strategies to relieve them.
Forensic Analysis
When a security offense is supposed to occur, SOC Analysts execute forensic research to comprehend how the occasion arose, what was compromised, and how to prevent future events. It requires meticulous attention to detail and an organized technique for investigating security incidents.
Communication Skills
Practical communication is necessary for SOC Analysts, both for collaborating with their class and for informing non-technical stakeholders.

Incident Reporting
SOC Analysts must be capable of documenting and reporting security happenings apparently. It contains exact incident reports that explain what happened, how it was taken, and what steps are required to be taken next.
Stakeholder Communication
Communicating complicated technical components to non-technical stakeholders is essential. SOC Judges are required to justify security conditions and their consequence in a manner that is understandable and actionable for corporation managers and additional stakeholders.
Team Collaboration
SOC Analysts work closely with different IT and security professionals. Robust interpersonal skills and the knowledge to cooperate effectively with others are essential for a united and efficient security procedures team.
Problem-Solving Skills
Cybersecurity is an ever-evolving domain, and SOC Judges must be experts at cracking problems and considering their paws.

Quick Decision-Making
During a security incident, SOC Analysts must make quick decisions to contain and mitigate the threat. It requires confidence, persistence, and the capacity to think apparently beneath pressure.
Creative Thinking
Threat performers are continually developing new methods to avoid security averages. SOC Analysts must be resourceful and innovative in their strategies for detecting and responding to these growing threats.
Root Cause Analysis
After managing a quick threat, SOC Judges require achieving an individuality cause analysis to learn how the incident happened and what can be accomplished to prevent similar problems in the future. It demands an in-depth knowledge of the underlying systems and approaches.
Continued Learning and Transformation
The cybersecurity geography is continuously varying, with new dangers and technologies appearing regularly. SOC Judges must be dedicated to continued learning and skilled development.

Keeping Up with Industry Trends
SOC Judges are required to remain knowledgeable about the most delinquent cybersecurity trends, dangerous geographies, and specialized advances. It affects reading industry journals, following discussions, and experiencing professional platforms and networks.
Pursuing Certifications
Certificates can validate a SOC Analyst’s skills and learning and are often required for profession advance. Some valuable certifications for SOC Analysts include CompTIA Security+, Certified Information Systems Security Professional, and Certified Ethical Hacker.
Tools and Technologies Used by SOC Analysts
Security Operations Center (SOC) Analysts depend on a various collection of tools and technologies to achieve their necessary assignments. These tools encourage them to monitor network traffic, notice potential threats, react to happenings, and analyze security data. Here, we will explore some of the necessary devices and technologies that are essential for Security Operations Center (SOC) Judges.

Security Information And Event Management Systems
SIEM strategies are the cornerstone of a SOC Analyst’s toolkit. They collect and analyze log data from numerous sources, such as waitpeople, network devices, and applications, providing a concentrated view of security occurrences. SIEM systems help SOC Analysts notice anomalies, correlate occurrences, and identify potential security incidents in real-time. Determined SIEM appliances retain Splunk and IBM QRadar.
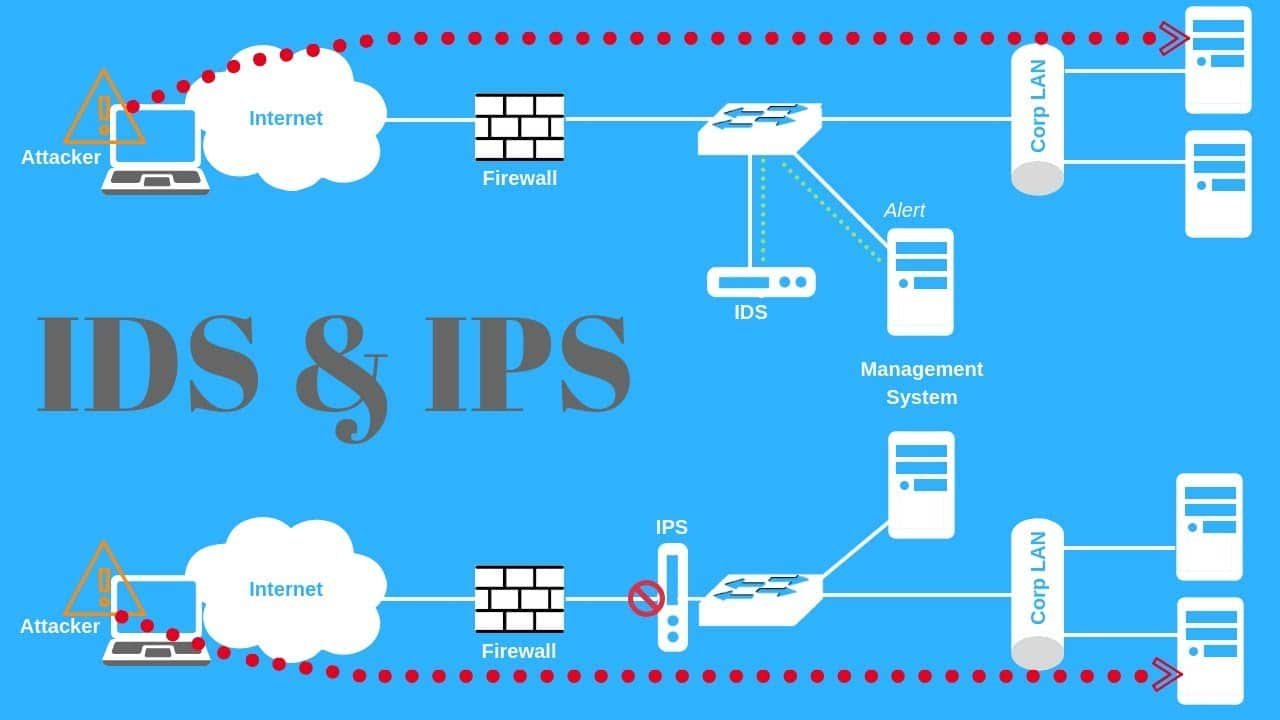
Intrusion Detection Systems and Intrusion Prevention Systems
IDS and IPS are essential for monitoring network traffic and recognizing opposing moves. IDS tools alert Security Operations Center (SOC) Analysts to suspect actions, while IPS tools can take proactive steps to secure or alleviate threats. These systems are essential for before detection and precluding of cyber attacks. Standards of IDS/IPS devices include Snort, Suricata, and Palo Alto Networks.
Firewalls
Firewalls are a whole security technology utilized to manage incoming and outgoing web gridlock established on prearranged protection laws. SOC Analysts configure and observe firewalls to guarantee they virtually protect the network edge. Firewalls help block unauthorized entrance and prevent adversarial traffic from penetrating the network.
Anti-virus and Endpoint Security Solutions
Anti-virus software and endpoint security keys protect unique devices from malware and additional cyber threats. SOC Analysts utilize these tools to notice, segregate, and remove opposing software from endpoints. These devices are paramount for possessing the security of all appliances attached to the web. Unique keys contain Symantec Endpoint Protection, McAfee, and CrowdStrike.
Threat Intelligence Platforms
Threat intelligence platforms deliver SOC Analysts with details on occurring threats, attack vectors, and arrows of compromise (IOCs). By incorporating threat intelligence into their procedures, SOC Analysts can improve their knowledge to detect and react to new and developing threats. Some widely used threat intelligence platforms are ThreatConnect, Anomali, and Recorded Tomorrow.
Forensic Tools
When a shield breach occurs, forensic tools are utilized to examine and analyze the incident. These tools enable Security Operations Center (SOC) Analysts to choose how the violation occurred, what systems were concerned, and what data may have been compromised. Forensic research is crucial for understanding the extent of the happening and deterring future events. Popular forensic tools include EnCase, FTK (Forensic Toolkit), and SANS Investigative Forensics Toolkit (SIFT).
Log Management Systems
Log management systems collect, store, and manage log data from various sources. SOC Analysts use these systems to examine logs for indications of suspicious movement and to sustain happening investigations. Effective log management is essential for preserving an audit trail and securing compliance with regulatory prerequisites. Standards of log management devices include LogRhythm, Graylog, and ELK Stack (Elasticsearch, Logstash, Kibana).
Network Traffic Analysis Tools
Network traffic analysis tools encourage SOC Analysts to scan and examine web traffic in real time. These tools help determine unique practices or manners that could suggest a security threat. Network traffic research is required for detecting progressive persistent threats (APTs) and additional cultivated attacks. Unique devices of this classification include Wireshark, NetFlow Analyzer, and SolarWinds.
Conclusion
The position of a Security Operations Center (SOC) Judge is difficult and rewarding. These experts are at the forefront of protecting communities against cyber dangers, guaranteeing data safeguards, and supporting business continuity. With suitable skills, education, and faith, a profession as a SOC Analyst suggests multiple prospects for development and improvement.








