
Connecting data is essential in today’s digital era. With cyber threats on the stage, the requirement for robust encryption techniques has never been more consequent. One such method, known for its significance and reliability, is understanding asymmetric encryption. This guide will explore the complexity of asymmetric encryption, justifying its regulations, applications, and importance in protecting susceptible knowledge.
What is Asymmetric Encryption?
Asymmetric encryption, also known as public-key cryptography, is a strategy for encrypting and decrypting data using a team of general and secret keys. Unlike symmetric encryption, which uses a single key for encryption and decryption, asymmetric encryption utilizes two different keys that are mathematically associated. This approach provides an additional security coating, making it a selected selection for various applications.
Historical Background
The concept of asymmetric encryption dates back to the 1970s, with considerable service from cryptographers like Whitfield Diffie and Martin Hellman. Their assignment applied the basis for current encryption techniques, revolutionizing how data is attached and communicated.
How Asymmetric Encryption Works
At its core, asymmetric encryption concerns generating a fundamental pair, a public key that is genuinely communicated, and a private key that stays hidden. Here’s a simple analysis of the process:
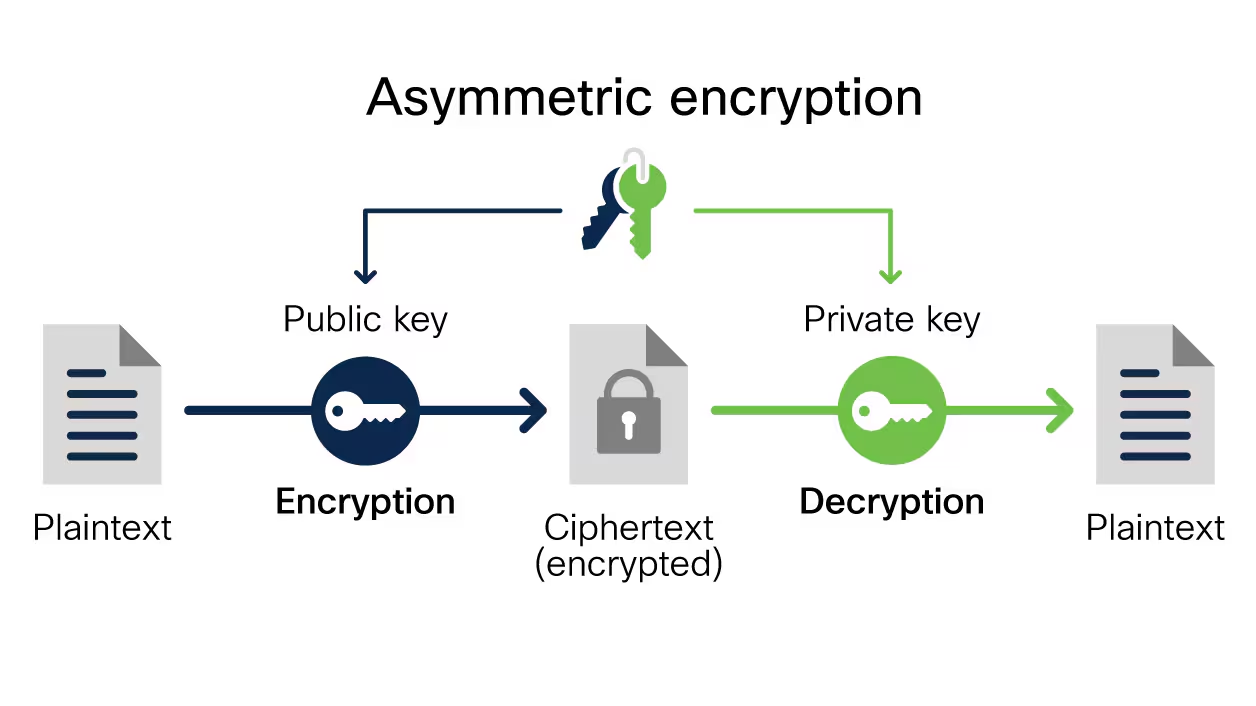
Encryption: An exporter operates the recipient’s public key to encrypt the transmission.
Decryption: The recipient then operates their private key to translate the message.
This dual-key system ensures that the data remains secure if the public key is widely assigned, as only the private key can decrypt the information.
Public Key and Private Key
In asymmetric encryption, the concepts of public and private keys are fundamental. These keys work together to secure communication and data. The public key is a cryptographic key that is sincerely shared and operated to encrypt data. It can be allocated widely without compromising security, authorizing anyone to send an encrypted message to the key’s owner. The public key is like a locked mailbox; anyone can arrange a letter inside, but only the owner can extend it.
On the other hand, the critical proprietor keeps the private key secret, and decrypts encrypted data with the connected public key. This key is crucial for preserving the security of the communication, as it guarantees that only the planned recipient can access the encrypted knowledge. The private key also plays a vital function in digital signatures, allowing holders to prove their uniqueness or document authenticity. The security of the fundamental system relies on the confidentiality of the private key, making its protection critical. The public and private keys facilitate secure, encrypted communication and authentication in different digital applications.
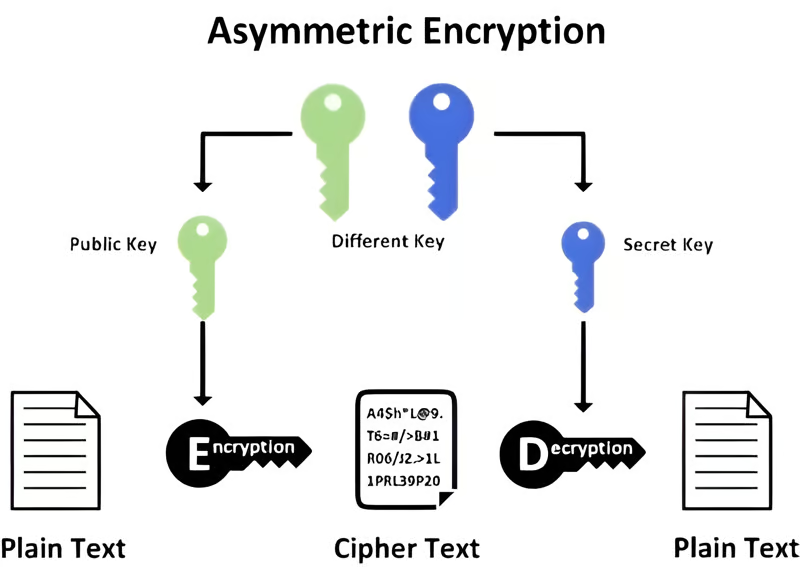
Understanding Public Key: The public key is general to anyone and is utilized to encrypt data. Securing the information so it can be securely sent to the planned recipient is required.
The Role of the Private Key: On the other hand, the owner keeps the private key secret. It is used to decrypt data that has been encrypted with the connected public key. The entire system’s security hinges on the confidentiality of this private key.
Applications of Asymmetric Encryption
Asymmetric encryption is versatile and finds use in various domains, including:
Secure Communication
It’s widely used to secure communications, ensuring that sensitive information, such as login credentials and personal data, remains confidential.
Digital Signatures
Asymmetric encryption is instrumental in creating digital signatures, which verify the genuineness and integrity of digital documents.
Data Integrity
It confirms that data has not been changed during communication, guaranteeing that the information acquired is as exact as sent.
Advantages of Asymmetric Encryption
Asymmetric encryption, also known as public-key cryptography, offers several advantages, making it a crucial tool in digital protection. One of its immediate benefits is improved security. Using a pair of keys, a public key for encryption and a private key for decryption, assures that if the public key the private key remains closed, thus shielding the data. This system also facilitates scalability, as public keys can be voluntarily distributed without compromising security, making it perfect for large-scale systems like the Internet.
Another significant advantage is non-repudiation. In asymmetric encryption, digital signatures can be designed to verify the authenticity and source of a message, ensuring that the sender cannot refuse to have transmitted the message. It is necessary for legal and financial transactions where realism is required. Additionally, asymmetric encryption sustains secure key exchange, enabling two details to select a secure communication channel without sharing a standard secret key beforehand. Combined with its robustness and flexibility, this feature makes asymmetric encryption a cornerstone of secure digital communication and data protection strategies.
Enhanced Security: The dual-key system provides a robust security framework, making accessing encrypted data challenging for unauthorized details.
Scalability: Asymmetric Encryption scales excellently with increasing users and machines, as individually can have its unique key pair.
Non-repudiation: It assures non-repudiation, suggesting that a sender cannot refuse to send a message, as the digital signature ensures the source.
Disadvantages of Asymmetric Encryption
Computational Complexity: One of the main disadvantages is its computational power, which can slow down processing times reached to symmetric encryption.
Slower Performance Compared to Symmetric Encryption: Asymmetric encryption typically requires additional computational resources, leading to slower Performance in real-time applications.
Asymmetric vs. Symmetric Encryption
Understanding Asymmetric and symmetric encryption are two fundamental cryptographic methods for securing data, each with distinct characteristics and applications.
Understanding Asymmetric encryption uses two keys: a public legend and a private decryption legend. These keys are mathematically connected. The private key stays secret, and the public key can be widely communicated. This system allows secure communication; even if the public key is exposed, only the personal key can decrypt the data. Asymmetric encryption is operated for secure key exchange, digital signatures, and small quantities of data, such as certifications or keys.
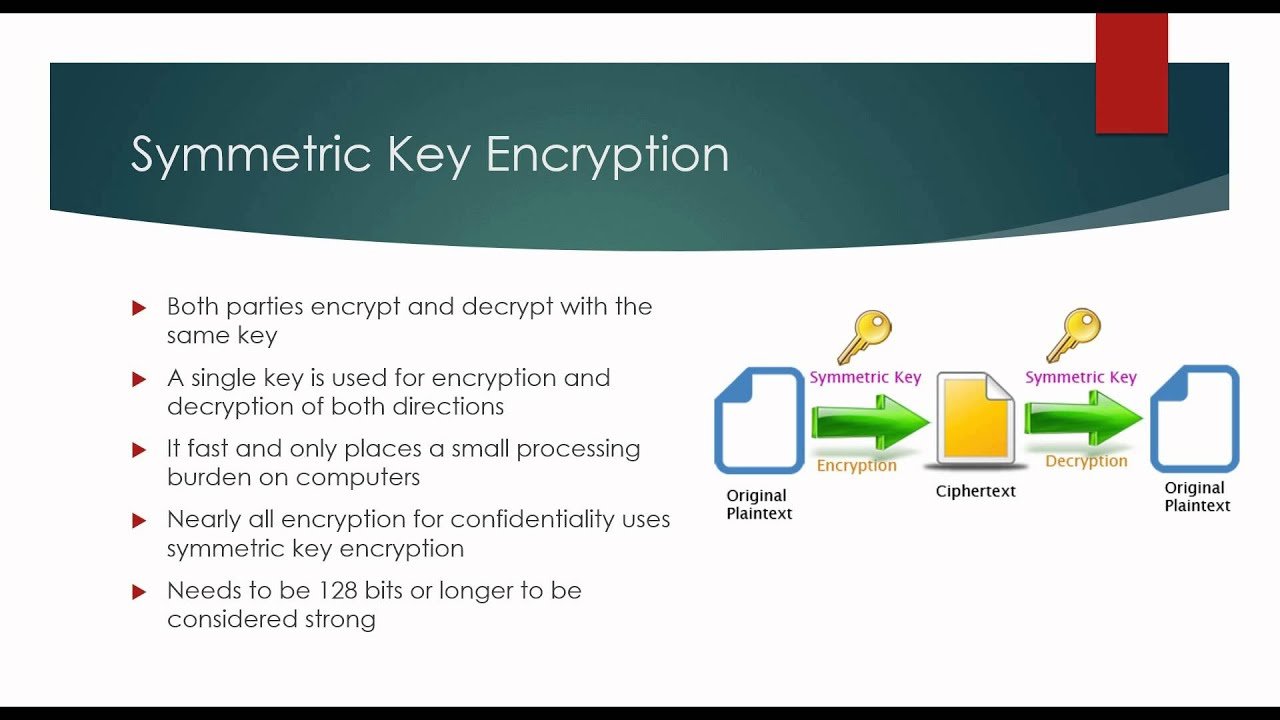
On the other hand, Symmetric Encryption operates a single key for both encryption and decryption. This method requires the sender and receiver to access the same secure secret key. Symmetric Encryption is commonly more immediate and slightly computationally intensive than asymmetric encryption, making it ideal for encrypting enormous volumes of data, such as entire files or disk purposes.
The choice between asymmetric and symmetric encryption largely depends on the specific use case. Generally, asymmetric encryption is often preferred for scenarios requiring secure key distribution and authentication. On the other hand, symmetric encryption is favored for its speed and efficiency in managing large datasets, making it ideal for applications where performance is critical.
In many current systems, these two methods are operated in a hybrid approach, leveraging stability to improve overall security.
Key Differences: The direct difference fibs in the critical system: Symmetric encryption works with a single key, while asymmetric encryption uses a couple of keys. This distinction impacts security and Performance.
Use Cases for Each: Symmetric Encryption is typically used for bulk data encryption due to its speed, whereas asymmetric encryption is preferred for securing communications and ensuring data integrity.
Standard Algorithms Used in Asymmetric Encryption
Several algorithms are commonly employed in asymmetric encryption, each with unique features and strengths:
RSA (Rivest–Shamir–Adleman)
One of the before and most widely used algorithms, RSA is comprehended for its strong security effects.
ECC (Elliptic Curve Cryptography)
ECC presents security similar to RSA but with fewer key sizes, making it more efficient in periods of computational capability.
DSA (Digital Signature Algorithm)
DSA is mainly used to create digital signatures, supplying a secure manner for authenticating digital documents.
Asymmetric Encryption in Everyday Life
Asymmetric encryption is an essential part of our daily digital exchanges, usually without us recognizing it:
Online Banking: Secures trades, protecting susceptible financial knowledge from unauthorized entry.
Email Encryption: Many email assistants use asymmetric encryption to safeguard the privacy of email ranges.
E-commerce Transactions: Asymmetric Encryption safeguards online transactions, ensuring that payment information remains confidential.
Security Considerations and Best Practices
While asymmetric encryption is highly secure, it’s crucial to follow best practices to maintain its effectiveness:
Key Management: Proper key management securely stores private keys and occasionally updates critical teams.
Avoiding Common Vulnerabilities: Awareness and mitigation of common vulnerabilities, such as weak key generation and poor critical storage practices, are vital for maintaining security.
The Role of Google NLP in Asymmetric Encryption
Google’s Natural Language Processing (NLP) tools can improve the Performance and knowledge of asymmetric encryption:
Natural Language Processing for Security Analysis: NLP can help analyze security protocols and determine potential defects in encryption systems.
Enhancing User Understanding: NLP tools can simplify complex encryption concepts, making it easier for users to understand and correctly use encryption technologies.
Asymmetric Encryption and Compliance
With increasing regulatory scrutiny, keeping with data security laws is essential:
GDPR and Data Protection: Asymmetric encryption mainly guarantees compliance with the agreement General Data Protection Regulation (GDPR), which requires stringent data safeguard standards.
Industry Standards and Regulations: For payment security, businesses using asymmetric encryption must adhere to industry measures and restrictions, such as PCI DSS.
The Future of Asymmetric Encryption
The occupation of encryption is continually developing, with new challenges and prospects on the horizon:
Quantum Computing and Its Impact: Quantum computing poses conceivable threats to present encryption techniques, necessitating the development of quantum-resistant algorithms.
Innovations and Emerging Trends: Ongoing analysis and innovation in encryption technologies continually vow to improve security and performance. Therefore, these advancements ensure the continued applicability of asymmetric encryption.
Conclusion
Asymmetric encryption is a cornerstone of contemporary digital security, providing a solid framework for protecting exposed data. Its applications are vast and vital, from secure communication to digital signatures. As technology develops, so will the techniques we use to guarantee our knowledge, with understanding asymmetric encryption persisting to play a vital part.








